What Is a Hardware Firewall? How It Works + When to Use One
A hardware firewall is a dedicated physical device that enforces security policies by filtering traffic between trusted and untrusted networks. It inspects packets as they pass through network boundaries and allows or blocks them based on defined rules.
Its functions are delivered through dedicated hardware and a purpose-built operating system designed for consistent performance as a stand-alone appliance.
How does a hardware firewall work?
A hardware firewall works as a stand-alone appliance placed at the edge of a network.
Here's an example of what it can look like:
A hardware firewall has its own processors, memory, interfaces, and operating system that are dedicated entirely to inspecting and controlling traffic. All packets entering or leaving the protected network must flow through its physical ports, which means the device becomes the checkpoint between trusted and untrusted zones.
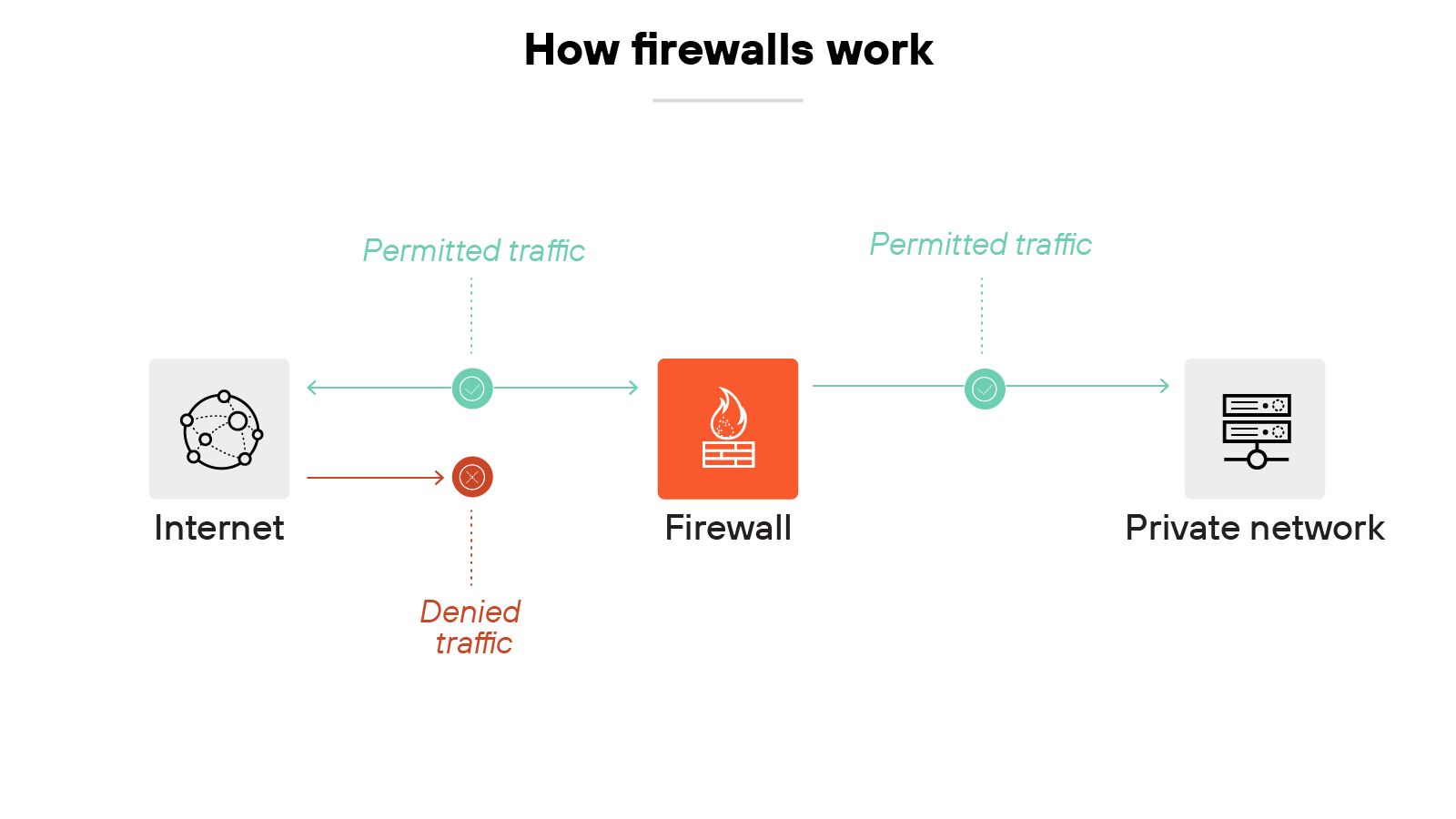
The firewall enforces security rules as traffic passes through. At a basic level, it uses packet filtering to compare header information such as addresses and ports against an approved rule set.
Like so:
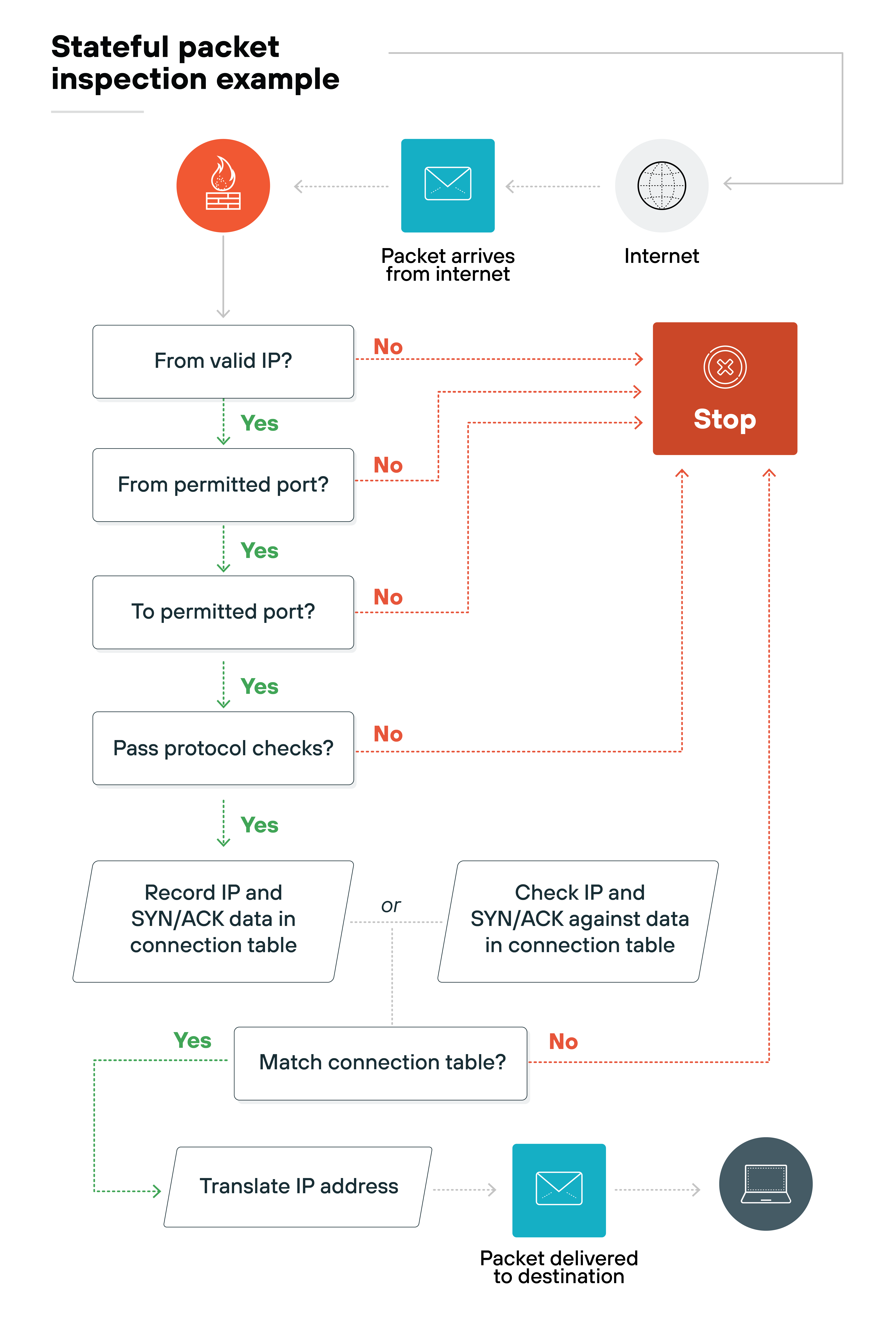
Most modern devices also perform stateful inspection. This allows the appliance to track active sessions and only permit packets that belong to a valid connection. In other words, the device doesn't just check individual packets. It understands their context within a session.
Here's how it works:
Hardware firewalls use dedicated physical components to perform deep packet inspection. They can analyze packet payloads, identify applications, and enforce policies at higher layers of the OSI model. Many appliances integrate features such as intrusion prevention and SSL inspection, which help block hidden or evasive threats.
Processing is handled by custom chips, such as ASICs or NPUs, that accelerate packet inspection and cryptography. The chassis often includes redundant elements like power supplies, fans, and interface cards to ensure continuity if a component fails.
These design traits allow hardware firewalls to deliver consistent throughput independent of shared host resources.
Basically, the hardware firewall works by forcing all network traffic through a purpose-built device that inspects, tracks, and enforces rules at multiple layers before allowing it to pass.
What do hardware firewalls offer?
A hardware firewall is distinct because it's delivered as a dedicated appliance rather than as software installed on general-purpose systems. That form factor brings its own characteristics.
For one, the device runs on purpose-built hardware.
Processing power, memory, and network interfaces are dedicated to packet inspection and policy enforcement. Because resources are dedicated to firewall tasks, performance is predictable within the rated capacity.
Another distinction is physical connectivity.
Hardware firewalls provide multiple copper or fiber interfaces. They can be placed inline between networks and configured to support bypass ports, VLAN segmentation, or redundant uplinks.
Finally, hardware delivery supports turnkey operational and compliance needs (turnkey, out of the box).
Devices can be certified under standards such as FIPS, housed in tamper-resistant chassis, and physically controlled in data centers. These are requirements that can't be met in the same way by virtual or cloud-only firewalls.
Ultimately, the security functions are the same across firewall hardware, software, and cloud models.
Hardware firewalls vs. software and cloud firewalls
All firewalls share the same inspection logic. They evaluate traffic, compare it to policy, and allow or block connections.
The differences lie in how the firewall is delivered and where it can be deployed.
| Hardware firewalls vs. software and cloud firewalls |
|---|
| Factor | Hardware firewall | Software firewall | Cloud firewall |
|---|---|---|---|
| Form factor | Physical appliance with dedicated CPU, memory, and interfaces | Runs as a process on servers, VMs, or containers | Runs in cloud provider infrastructure or delivered as Firewall as a Service (FWaaS) |
| Deployment | Installed at network perimeters such as data centers or campuses | Installed in virtualized data centers, branches, or container platforms | Deployed directly in public cloud environments or consumed as a managed service |
| Performance model | Predictable throughput based on purpose-built hardware | Shares resources with host environment; scalable through orchestration | Elastic scaling within cloud infrastructure; dependent on provider resources |
| Policy enforcement | Centralized at the edge; applies rules consistently across devices on the internal network | Applied close to workloads; supports segmentation and east–west traffic control | Applied inside cloud workloads; ensures consistency across multi-cloud environments |
| Operational considerations | Requires physical setup, refresh cycles, and hardware management | Flexible, automated deployment; integrates with DevOps and orchestration tools | Reduces local management; relies on provider availability and service model |
In short:
- Hardware firewalls excel at anchoring fixed network boundaries with dedicated performance and physical control.
- Software firewalls extend protection into virtualized and distributed environments.
- Cloud firewalls adapt the same functions for workloads and applications hosted in public cloud platforms.
Each firewall model addresses different deployment needs, and many organizations use them together for comprehensive coverage.
- Hardware Firewalls vs. Software Firewalls
- What Is a Software Firewall? Why It's Needed + How It Works
- What is a Public Cloud Firewall?
- What Is Firewall as a Service (FWaaS)? | FWaaS Defined & Explained
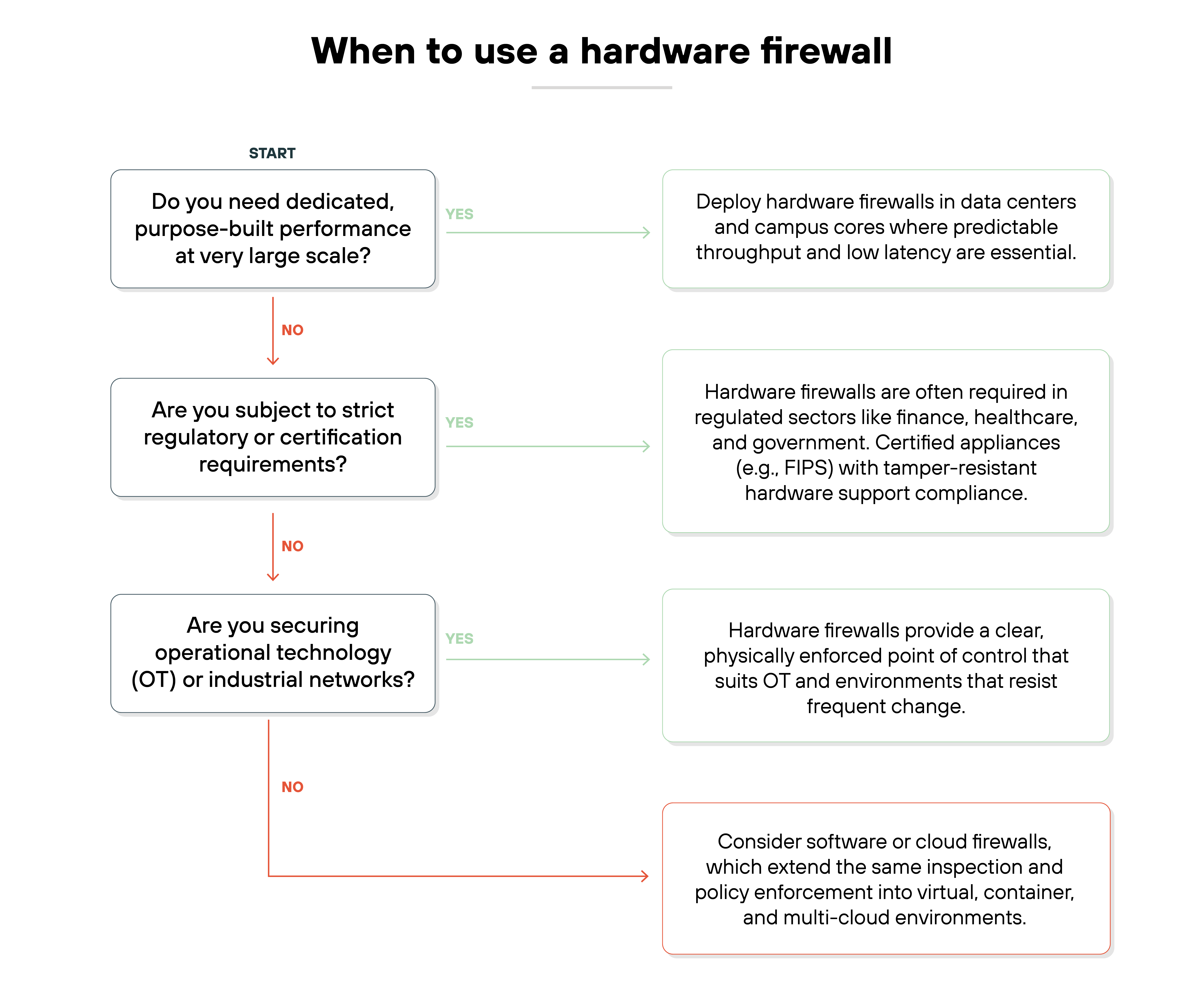
When should you use a hardware firewall?
Hardware firewalls remain the most common form factor in enterprise networks. They continue to serve as the foundation for many firewall strategies.
Why?
As discussed, a physical device provides predictable performance. It's purpose-built to handle inspection at scale, which makes it well suited for data centers and campus cores. If an organization needs to process large volumes of traffic with low latency, a hardware firewall is a practical choice.
Plus, regulated industries often require appliances with specific certifications. Again, hardware devices can be validated for standards such as FIPS. They can also be housed in tamper-resistant chassis and placed under physical control. These characteristics make them attractive to sectors like finance, healthcare, and government.
Operational technology and industrial networks are another area. In these environments, reliability and physical enforcement at the network boundary are critical. A stand-alone device provides a clear point of control in systems that may not tolerate frequent change.
Remember: This doesn't mean hardware is always the only answer.
Software and cloud firewalls extend the same functions into places where appliances cannot be deployed. Together, the models complement each other.
To sum up: Hardware firewalls should be used whenever predictable performance, physical control, or regulatory compliance are the main priorities. They continue to anchor enterprise security while other form factors expand coverage into new environments.
