- 1. What does the industry really mean by “quantum security”?
- 2. Why won't today's encryption hold up against quantum computers?
- 3. What is post-quantum cryptography, and why is it relevant?
- 4. Where do QKD and QRNG fit into quantum security?
- 5. Why is quantum security so challenging to put in place?
- 6. How are organizations getting quantum ready today?
- 7. Is the quantum threat imminent — or still years away?
- 8. Quantum security FAQs
- What does the industry really mean by “quantum security”?
- Why won't today's encryption hold up against quantum computers?
- What is post-quantum cryptography, and why is it relevant?
- Where do QKD and QRNG fit into quantum security?
- Why is quantum security so challenging to put in place?
- How are organizations getting quantum ready today?
- Is the quantum threat imminent — or still years away?
- Quantum security FAQs
What Is Quantum Security? Preparing for the Post-Quantum Era
- What does the industry really mean by “quantum security”?
- Why won't today's encryption hold up against quantum computers?
- What is post-quantum cryptography, and why is it relevant?
- Where do QKD and QRNG fit into quantum security?
- Why is quantum security so challenging to put in place?
- How are organizations getting quantum ready today?
- Is the quantum threat imminent — or still years away?
- Quantum security FAQs
Quantum security is the practice of protecting information and communications from the risks created by quantum computing. It focuses on replacing cryptographic methods such as RSA and ECC that could be broken by quantum algorithms.
The discipline recognizes post-quantum cryptography as the main solution, alongside research into quantum-based approaches like quantum key distribution.
What does the industry really mean by “quantum security”?
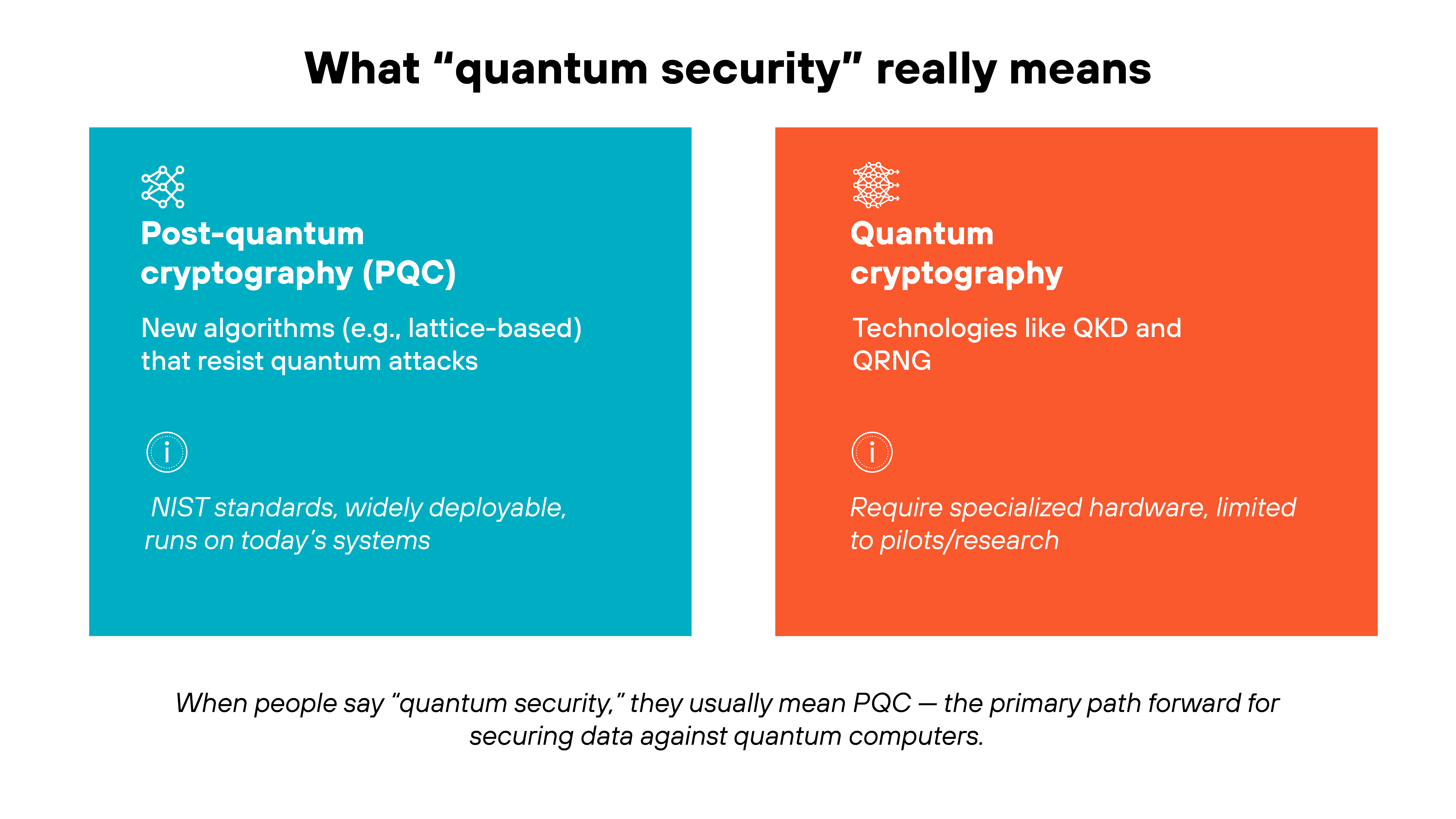
The phrase quantum security often gets used loosely. Some treat it as if it covers every quantum-related technology in cybersecurity. But in practice, most of the security community uses it as shorthand for one thing: post-quantum cryptography.
In other words:
“Quantum security” usually refers to the transition away from encryption methods like RSA (Rivest–Shamir–Adleman) and ECC (Elliptic-curve cryptography).
These are the methods that could be broken by large-scale quantum computers running algorithms such as Shor’s. Post-quantum cryptography, or PQC, focuses on new mathematical approaches that can withstand both classical and quantum attacks.
So why do you also hear about things like quantum key distribution (QKD) and quantum random number generators (QRNGs) ?
Because they’re genuine quantum innovations that are already being tested in specialized networks and hardware systems. However, they rely on dedicated optical or quantum components, which makes large-scale deployment difficult today. As a result, QKD and QRNG remain focused on high-assurance or research environments, while PQC provides the software-based path most organizations can adopt now.
Understanding why PQC is recognized as the main path forward requires looking at the risk itself.
More specifically, the encryption that secures internet traffic, banking, healthcare records, and digital identities depends on problems that quantum algorithms are expected to solve.
That’s why the standards community, led by NIST, has focused on advancing PQC first.
Why won't today's encryption hold up against quantum computers?
The encryption used to protect most digital systems today was designed with classical computers in mind.
Common algorithms like RSA and elliptic curve cryptography rely on mathematical problems that are extremely difficult for current machines to solve. And that difficulty is what makes the encryption strong.
Quantum computers change the equation.
They use principles of quantum mechanics that allow certain problems to be solved far faster than classical machines ever could. Which means the math that underpins RSA and ECC is no longer safe once large-scale quantum computers exist.
Here's why.
A quantum algorithm called Shor's can factor large numbers and compute discrete logarithms efficiently. And those are the exact problems that make RSA and ECC secure today.
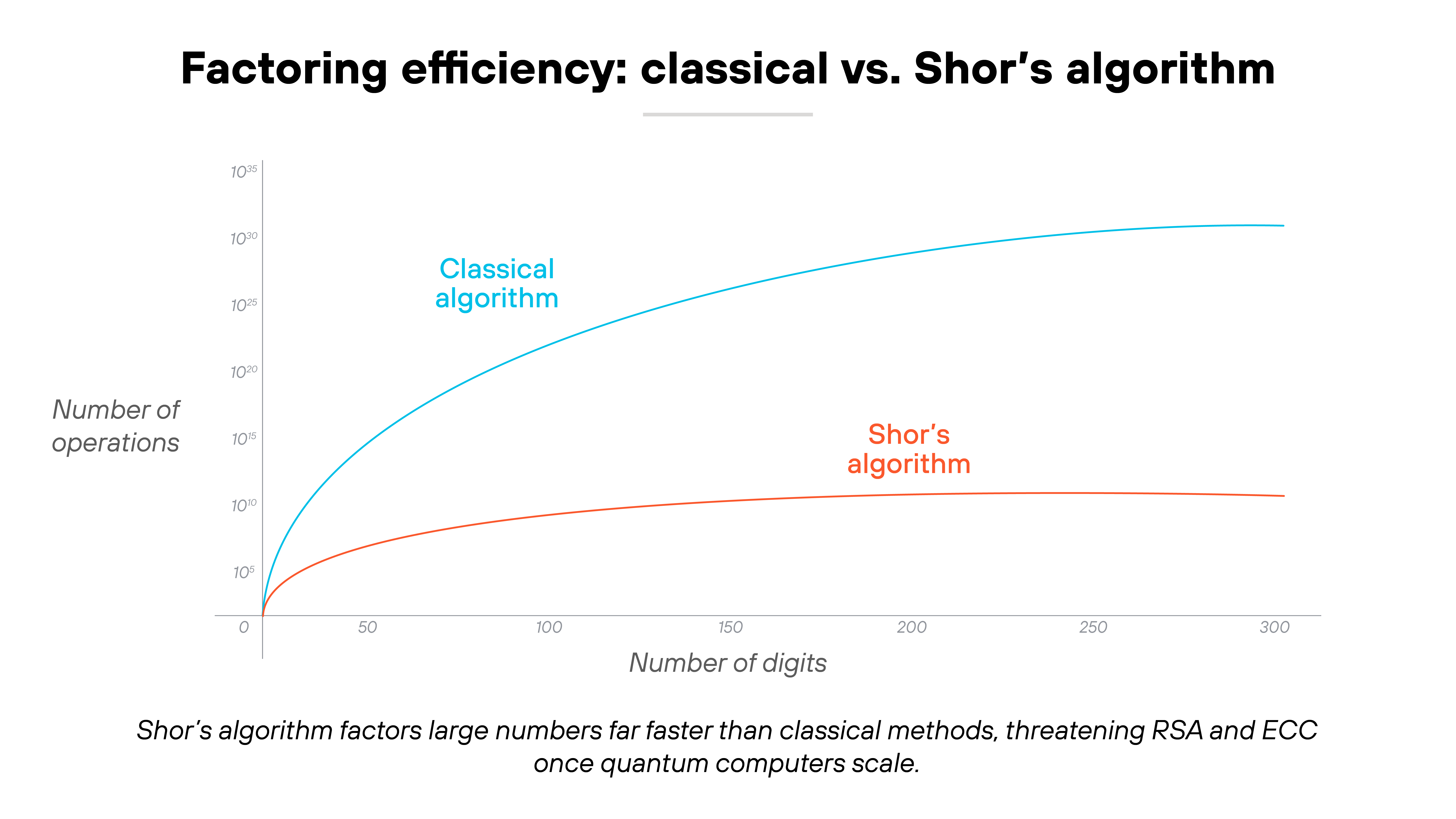
So if an attacker had a sufficiently powerful quantum computer, they could use Shor's algorithm to break these systems outright. The effect would be immediate: encrypted traffic, digital signatures, and authentication systems that rely on RSA or ECC could be forged or exposed.
Symmetric encryption such as AES is affected too, though in a different way.
Another algorithm, Grover's, reduces the effective strength of symmetric keys by half. A 256-bit key would provide the equivalent of 128-bit security against a quantum attack. In other words, quantum computers make brute force attacks faster.
The good news: AES can remain secure with larger key sizes, which is why 256-bit AES is expected to continue protecting data even in a quantum era. This makes symmetric encryption more resilient than RSA or ECC, though it still requires updates to key management practices.
That said, the danger isn't only in the future.
Attackers can capture encrypted data now and hold onto it until quantum computers mature. This is called harvest now, decrypt later. Sensitive information with long-term value, like financial records or government communications, could be exposed even if it's stored securely today.
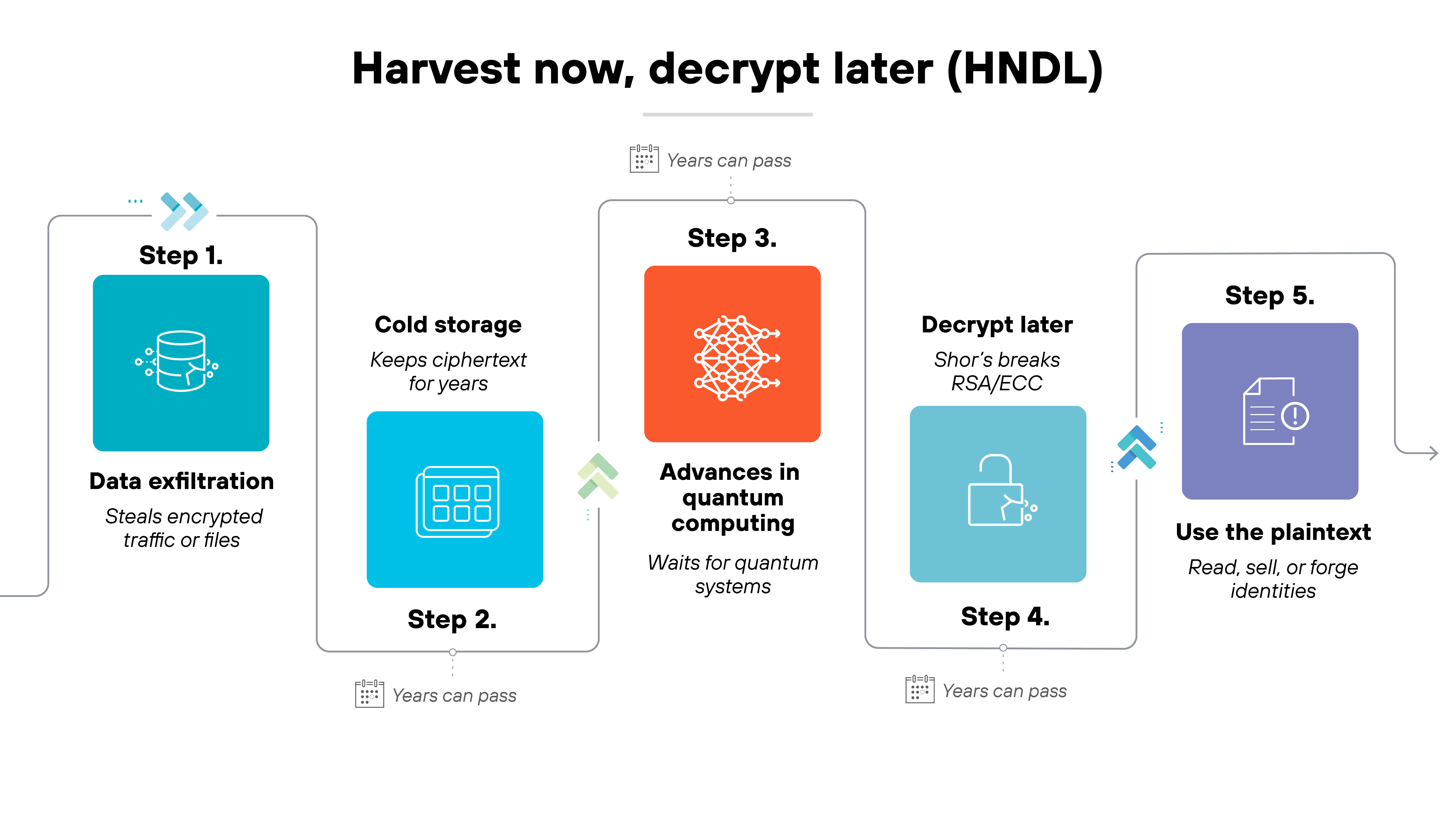
That's exactly why there's so much focus on quantum security.
The core concern is that the encryption protecting internet traffic, digital identities, and critical systems will not stand up once quantum computing reaches a practical scale. So cryptographic standards are being developed to protect against these risks.
- 8 Quantum Computing Cybersecurity Risks [+ Protection Tips]
- Harvest Now, Decrypt Later (HNDL): The Quantum-Era Threat
What is post-quantum cryptography, and why is it relevant?
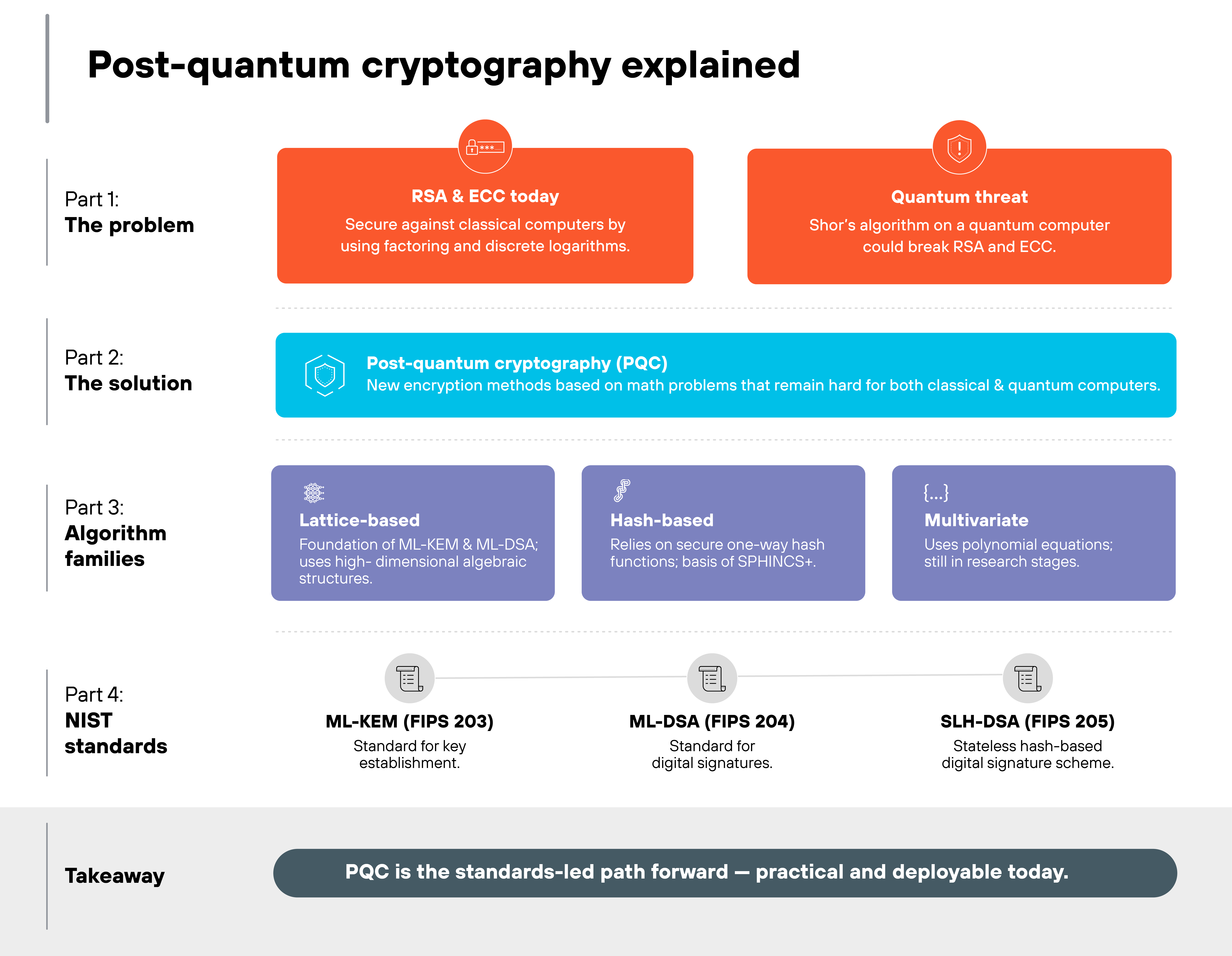
Post-quantum cryptography, or PQC, is a set of encryption methods designed to remain secure even when large-scale quantum computers exist. It provides the same functions as today's cryptography—like securing web traffic and digital signatures—but uses different mathematical foundations.
Here's the key difference.
RSA and elliptic curve cryptography depend on factoring and discrete logarithms. These are math problems that take classical computers so long to solve that they're considered secure in practice.
But they're easy for a quantum computer running Shor's algorithm.
So PQC avoids those weak points by relying on different kinds of problems that remain difficult for both classical and quantum systems. By changing the underlying math, PQC can provide the same functions as today's encryption without breaking once quantum computers reach scale.
So what does that look like in practice?
Researchers are working with several different families of algorithms:
Lattice-based cryptography is one of the main approaches. It uses high-dimensional algebraic structures that even a quantum computer cannot solve efficiently.
Other families, like hash-based and multivariate cryptography, offer additional options.
The important point is that all of these algorithms can run on today's classical machines. Which means organizations don't need quantum hardware to start adopting them.
To make adoption practical, NIST has standardized three algorithms for real-world use:
Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM) is used for key establishment.
Module-Lattice-Based Digital Signature Algorithm (ML-DSA) is used for digital signatures.
Stateless Hash-Based Digital Signature (SLH-DSA) is a stateless hash-based signature scheme built on the SPHINCS+ design.
These algorithms are expected to become the backbone of future secure communications.
The takeaway is this:
PQC isn't experimental. It's the mainstream, standards-led path forward. While physics-based methods like quantum key distribution are interesting, PQC is the deployable solution that enterprises, governments, and vendors are preparing to implement now.
- What Is Post-Quantum Cryptography (PQC)? A Complete Guide
- A Complete Guide to Post-Quantum Cryptography Standards
Where do QKD and QRNG fit into quantum security?
Technologies like quantum key distribution (QKD) and quantum random number generators (QRNGs) often come up in conversations about quantum security.
They’re featured in research, standards development, and pilot projects—especially in telecom and government networks—so it’s easy to assume they’ll define the future of secure communication.
Here's the reality.
Quantum cryptography is different from post-quantum cryptography. PQC is about new mathematics that can run on today's classical machines. Quantum cryptography, on the other hand, uses the physics of quantum mechanics itself.
The best-known example is QKD.
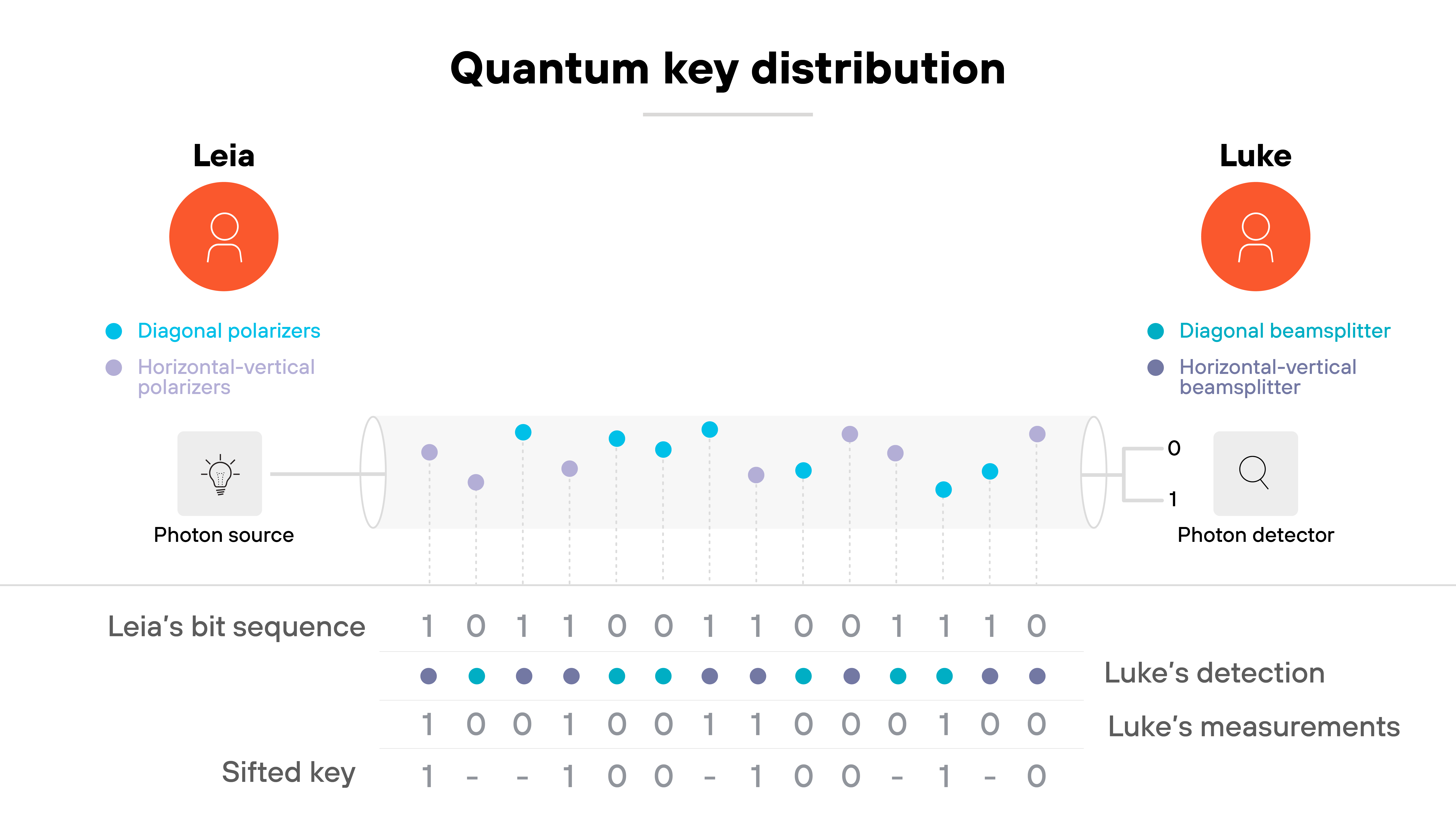
It lets two parties exchange encryption keys by transmitting photons in quantum states. If anyone tries to intercept the transmission, the quantum state changes. That disturbance alerts the sender and receiver that the key has been compromised.
In simple terms, eavesdropping becomes detectable. But while this provides a new level of assurance, it also requires very specialized hardware that makes it hard to scale.
QRNGs work differently.
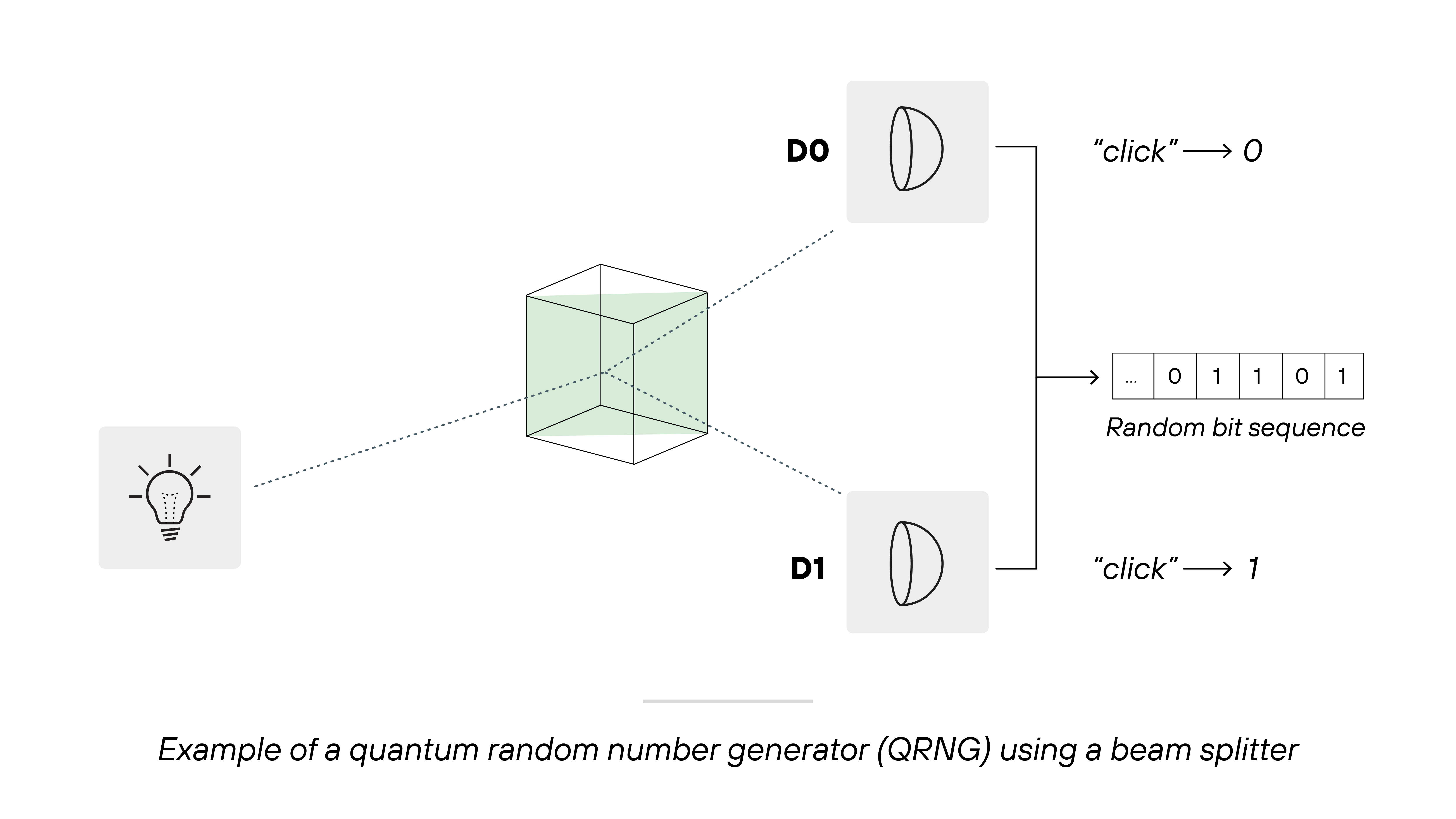
They harness unpredictable quantum processes to generate random numbers. Cryptography depends heavily on randomness, so better random numbers strengthen keys and reduce predictability. So QRNGs already have growing applications in hardware security modules and secure communications.
While both technologies are advancing, their adoption remains concentrated in specialized use cases. For most organizations, PQC offers the most practical, software-deployable path to quantum-safe security today, while QKD and QRNG continue to evolve as complementary technologies for high-assurance environments.
Why is quantum security so challenging to put in place?
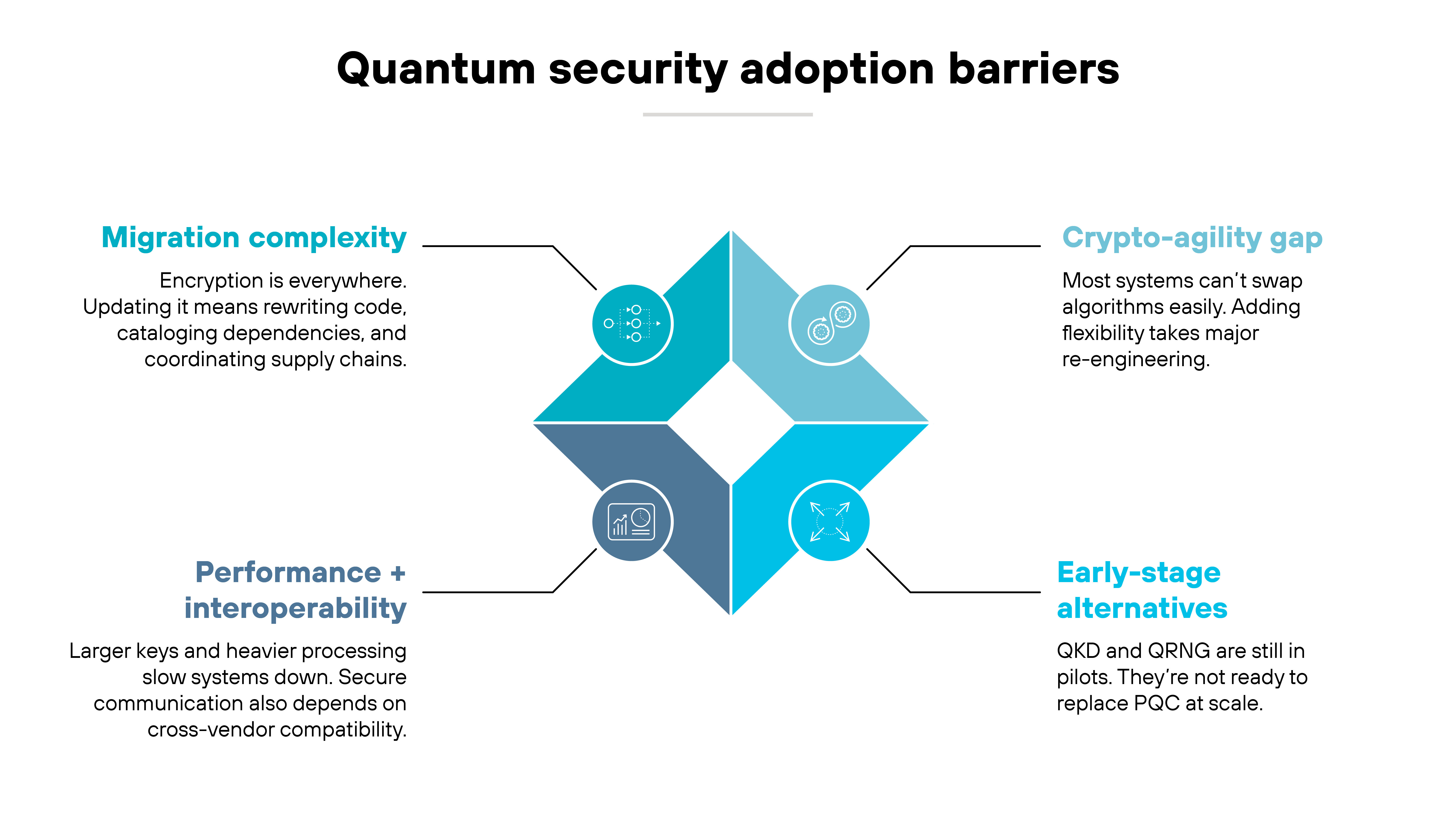
On paper, adopting quantum-safe protections sounds straightforward. In reality, it requires challenging, complex changes that will take years to implement.
The first challenge is migration.
Encryption is embedded in nearly every system, protocol, and application. Replacing algorithms isn't just a software update. It means cataloging every dependency, rewriting code, and coordinating across supply chains. Which means timelines stretch into years. Not months.
Performance is another hurdle.
Many post-quantum algorithms require larger keys and more processing. And that creates concerns about efficiency on constrained devices and in high-volume systems.
Plus, interoperability across networks and vendors adds another layer of difficulty. If systems can't communicate securely with each other, adoption stalls.
Then there’s the issue of crypto-agility.
Most systems today aren't designed to switch cryptographic algorithms easily. And that means migrations often require re-engineering entire architectures. The absence of this flexibility makes transitions slower and riskier.
Finally, there’s the early-stage nature of quantum-enabled approaches like QKD and QRNG.
They're still limited to pilots and niche deployments. As discussed, organizations can't rely on them as a broad solution.
To sum up: moving to quantum security isn't a one-time project. It's a gradual process that combines new standards, infrastructure updates, and operational changes. That's why governments and vendors emphasize preparation today, even though large-scale quantum computers may still be years away.
How are organizations getting quantum ready today?
It can't be said enough: quantum security isn't something that can be adopted overnight.
Even with NIST standards in place, moving from today's encryption to post-quantum algorithms requires careful planning and years of work. So most organizations are starting with small steps.
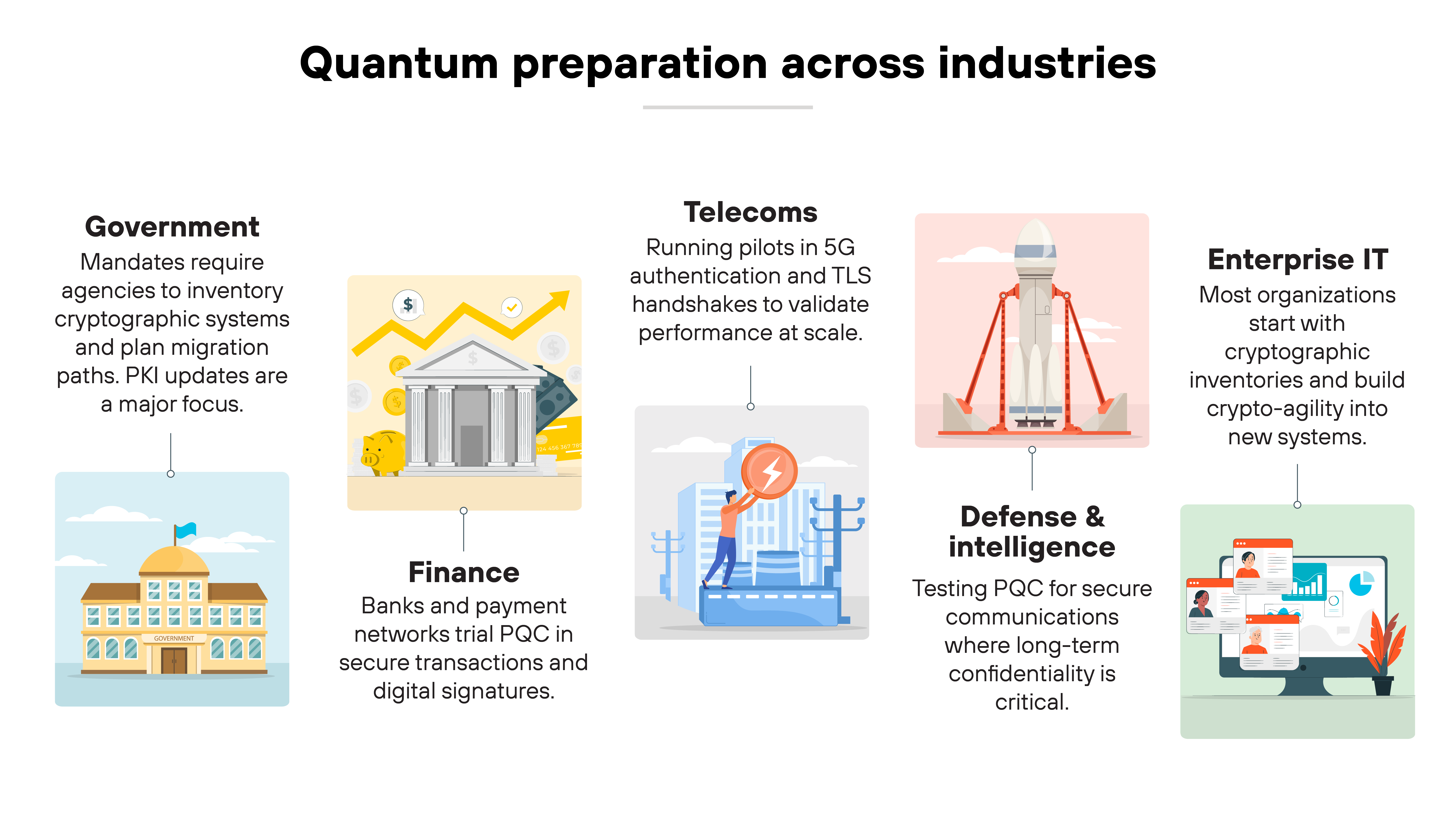
Governments are leading the way.
Some have issued mandates requiring agencies to begin inventorying cryptographic systems and planning migration paths.
Updates to public key infrastructure (PKI) are also a major priority, since certificates and trust hierarchies are some of the hardest components to transition. PKI migration is especially complex because it touches nearly every secure transaction, from websites to email to digital identities.
Defense and intelligence sectors are also testing PQC for secure communications where long-term confidentiality is critical.
Telecom providers are running pilots too.
PQC has been tested in 5G authentication and subscriber identity protection.
It's also been trialed in TLS handshakes by browser vendors and major libraries to test compatibility with secure web traffic.
These trials help validate how the algorithms perform at scale and in high-speed environments. They also highlight performance trade-offs and the need for hardware acceleration.
Financial institutions are exploring PQC as well.
Banks and payment networks are beginning to trial PQC in secure transactions and digital signatures. The goal is to protect sensitive data with long-term value, such as customer records and high-value financial contracts.
For most organizations, the first step is a cryptographic inventory.
That means cataloging where algorithms like RSA and ECC are embedded across infrastructure, applications, and vendor products. Without this visibility, planning a migration is almost impossible.
Another priority is building crypto-agility into new systems, as mentioned earlier.
That means designing infrastructure so algorithms can be swapped out quickly and at scale. Because even approved standards may face future weaknesses. So organizations need the ability to adapt without repeating costly rebuilds.
The bottom line: governments, telecoms, and finance are already running pilots and preparing for migration. Most organizations are still in the planning and inventory stage. The shift to quantum-safe cryptography will take time, but readiness efforts are well underway.
Is the quantum threat imminent — or still years away?
The quantum threat is already here.
As explained, encrypted data can be stolen today and unlocked later when quantum computers mature. The “harvest now, decrypt later” approach puts long-lived information—like medical files, financial records, and government communications—at risk.
The reality is that urgency really isn't about predicting when quantum computers will arrive. It's about the fact that data stolen now could still hold value in ten or twenty years, long after it's been compromised.
The timeline for large-scale quantum computers is still uncertain. Some predictions point to breakthroughs within a decade, while others suggest it could take much longer. But even if the exact date is unclear, the risk is already material.
That's why preparation can't wait.
Migrating cryptographic systems takes years. Algorithms need to be integrated into protocols, tested for performance, and deployed across vast infrastructures. Certificates and keys in public key infrastructures also have to be replaced.
And none of that can be done quickly.
The inflection point may not be pinned to a calendar. But the danger is already looming.
So organizations that begin preparing now will be ready when quantum computers reach scale. Those that wait risk being caught unprotected with years of work still ahead.
Get your quantum readiness assessment.
- Overview of your cryptographic landscape
- Quantum-safe deployment recommendations
- Guidance for securing legacy apps & infrastructure
