- What is Malware? Detecting, Preventing & Managing Threats
-
Malware vs. Exploits
-
What is Ransomware as a Service (RaaS)?
- What is Multi-Extortion Ransomware?
- What is Malware vs. Ransomware?
-
Expanding Targets for New SunOrcal Malware Variant
-
What Are Fileless Malware Attacks and “Living Off the Land”? Unit 42 Explains
What Is Malware Protection?
Malware protection is a set of security tools and practices designed to prevent, detect, and remove malicious software from computer systems and networks. This proactive defense mechanism safeguards data, maintains system integrity, and ensures the availability of resources against various cyber threats. It is a crucial component of a comprehensive cybersecurity strategy for both individuals and organizations.
Key Points
-
Malware protection is a broad term encompassing various defenses against malicious software. -
Layered security is the most effective approach, combining multiple technologies and practices. -
Behavioral analysis and machine learning are crucial for identifying new and unknown malware strains. -
Endpoint protection and network security are equally critical, as both are common vectors for infections. -
User education is a vital, non-technical component of any robust malware protection plan. -
Protection goes beyond traditional antivirus and includes more advanced solutions.
Malware Protection Explained
Malware protection encompasses a wide range of technologies and strategies that work together to defend against the evolving threat landscape. While traditional antivirus software primarily focused on signature-based detection of known viruses, modern malware protection extends to more sophisticated threats. This broader approach is necessary because today's malware is often fileless, polymorphic, or designed to bypass legacy defenses.
Modern malware protection is built on a proactive and adaptive framework. It combines a variety of techniques to create a multi-layered defense. This layered approach ensures that if one defense mechanism fails, others are in place to detect and mitigate the threat before it can cause significant damage.
How Malware Protection Works
Malware protection has evolved from a simple list of known threats to a complex, multifaceted defense system. It now combines several methods to identify and stop malicious code. The goal is to block known threats while also recognizing and neutralizing new, unknown threats.
Signature-Based vs. Behavioral Detection
Traditional antivirus software relies on signature-based detection, which works much like a criminal database. It compares the file's unique digital "signature" against a database of known malware.
While fast and effective for known threats, this method is useless against new, zero-day malware that has not yet been cataloged. Behavioral detection is a more advanced technique that watches for suspicious actions. Instead of looking for a signature, it monitors how a program behaves.
For example, a program attempting to encrypt a large number of files or disable security services would be flagged as a potential threat, regardless of whether its signature is known. This is a crucial defense against modern, fileless, and polymorphic malware.
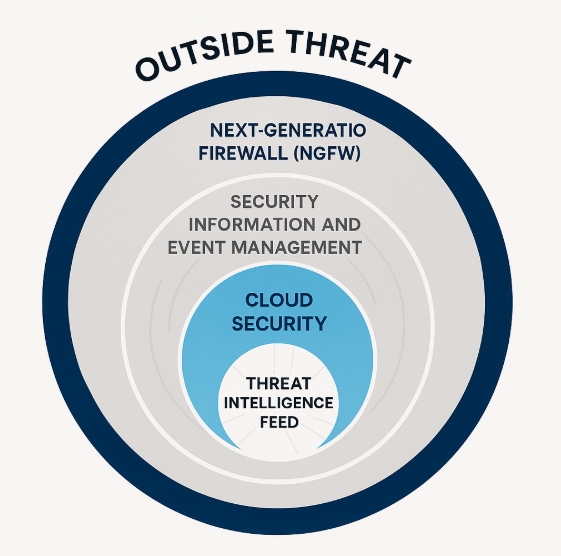
A Multi-Layered Approach to Defense
Effective malware protection is a multi-layered system, not a single tool. It integrates different technologies to provide overlapping security. This redundancy is essential for catching threats that may slip past one layer of defense.
Threat Intelligence
Threat intelligence acts as the eyes and ears of a security system. It collects and analyzes data on current and emerging cyber threats from various sources. This information helps security tools anticipate attacks and proactively update their defenses.
For example, Unit 42's threat research found that social engineering was the top initial access vector in 36% of their incident response cases between May 2024 and May 2025. This intelligence helps organizations prioritize defenses against human-centric attacks.
Network Protection
Network protection focuses on securing the perimeter of your digital environment. Next-generation firewalls (NGFWs) inspect network traffic for malicious content and block unauthorized access attempts. This layer stops threats from entering the network in the first place.
Endpoint Protection
Endpoint protection secures individual devices, such as laptops, desktops, and mobile phones. These solutions serve as the last line of defense, employing a combination of behavioral analysis, machine learning, and signature-based detection to stop malware that has evaded other security layers. Endpoint Detection and Response (EDR) is an evolution of traditional endpoint security, providing deeper visibility and response capabilities.
Cloud and SaaS Security
As more organizations move to cloud-based services, securing these environments is a critical layer of malware protection. Cloud and Software-as-a-Service (SaaS) security solutions monitor data and applications in the cloud. They protect against misconfigurations, unauthorized access, and malware designed to target cloud infrastructure.
The Role of Sandboxing and Heuristics
Sandboxing is a technique that isolates suspicious files in a safe, virtual environment. The file is allowed to run, and its behavior is carefully monitored. If the file performs malicious actions, such as attempting to modify system files or connect to a command-and-control server, it is identified as malware and blocked. This is an excellent way to analyze unknown files without risking the host system.
Heuristic analysis is another key component that uses a set of rules and algorithms to detect potential malware. It looks for characteristics that are common to malicious software.
For example, a file might be flagged for using code obfuscation or attempting to modify the registry in an unusual manner. While it can produce false positives, it is a powerful tool for catching new and unique threats.
Key Components of an Enterprise Malware Protection Strategy
A comprehensive enterprise malware protection strategy goes far beyond basic antivirus software. It involves a suite of interconnected technologies designed to provide a cohesive defense. These components work together to detect, prevent, and respond to threats across the entire network.
Endpoint Detection and Response (EDR)
EDR is an advanced security solution that provides real-time monitoring and analysis of endpoint activity. Unlike traditional antivirus software that simply blocks threats, EDR offers deep visibility into what is happening on a device. It can track a malware's activity from initial entry to a full-blown attack. This enables security teams to investigate and contain threats more effectively, as well as to understand the full scope of a breach.
Next-Generation Firewalls (NGFWs)
Next-generation firewalls (NGFWs) are a crucial component of network protection. They go beyond basic packet filtering to provide deep packet inspection, intrusion prevention, and application awareness.
An NGFW can identify and block malicious traffic based on the application it is using, not just the port. It can also integrate with threat intelligence feeds to block communication with known malicious IP addresses and domains.
Security Information and Event Management (SIEM)
A Security Information and Event Management (SIEM) system is a centralized tool for managing and analyzing logs. It collects security data from various sources across the network, including endpoints, firewalls, and servers.
By correlating and analyzing this data, a SIEM can detect complex attack patterns that would be invisible to individual security tools. This enables a comprehensive view of the security landscape and facilitates faster incident response.
User and Entity Behavior Analytics (UEBA)
UEBA systems use machine learning to establish a baseline of normal user and device behavior. When a user or device deviates from this baseline, the system flags the activity as suspicious. For example, a UEBA tool would detect if an employee suddenly started accessing sensitive data they do not normally access. This is a powerful way to identify insider threats and compromised accounts, even if no malware signature is present.
Common Types of Malware Threats
The threat landscape is constantly evolving, with new types of malware emerging regularly. Understanding the most common threats is crucial for building an effective defense. Modern malware is often sophisticated and designed to evade detection.
Top Threats Facing Organizations
Ransomware
Ransomware is a type of malware that encrypts a victim’s files and demands a ransom payment to restore access. It has become one of the most significant threats to businesses globally. The attack often begins with a phishing email or a vulnerability in an unpatched system. A notable example is the NotPetya attack of 2017, which spread rapidly and caused over $10 billion in damages globally, paralyzing major companies like Maersk and FedEx.
Phishing and Social Engineering
Phishing is a social engineering technique used to trick users into revealing sensitive information or downloading malware. Attackers send fraudulent emails or messages that appear to be from a legitimate source. These messages often contain malicious links or attachments that deliver malware to the user's system.
According to Unit 42, 66% of social engineering attacks in 2025 targeted privileged accounts, highlighting the critical need for comprehensive identity and access management.
Fileless Malware
Unlike traditional malware, which relies on a file, fileless malware operates directly in a computer’s memory and utilizes legitimate tools already present on the system. It leaves no footprint on the hard drive, making it difficult for signature-based antivirus solutions to detect. This type of malware is a growing concern, highlighting the need for behavioral analysis.
Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are targeted attacks conducted by highly skilled attackers. They gain access to a network and remain undetected for an extended period to steal data or disrupt operations. APTs often use a combination of different techniques, including custom-made malware, to evade detection.
The Evolving Threat Landscape
AI-Powered Attacks
Attackers are now utilizing artificial intelligence to enhance the sophistication of their attacks. AI can automate the creation of new malware variants and enhance social engineering campaigns. It also allows attackers to quickly identify vulnerabilities in a network, making attacks more efficient.
IoT and Mobile Malware
With the proliferation of Internet of Things (IoT) devices and mobile devices, new attack vectors are emerging. IoT devices are often poorly secured, making them a prime target for botnets and other malware. Mobile malware, designed to target smartphones and tablets, is also on the rise, often stealing personal data or financial information.
Supply Chain Attacks
A supply chain attack targets an organization by compromising one of its trusted suppliers. The attacker injects malicious code into a legitimate software update or product. When the software is distributed, the malware is delivered to the unsuspecting victim, bypassing traditional defenses.
Implementing Effective Malware Protection
Building an effective malware protection strategy requires a combination of technology, processes, and people. It's not just about installing software; it's about creating a culture of security and continuous vigilance. A proactive approach is always more effective than a reactive one.
Best Practices for Businesses
Regular Software and System Updates
One of the simplest and most effective ways to prevent malware is to keep all software and operating systems up to date. Patches often fix vulnerabilities that malware exploits. Automating this process ensures that all devices on the network are protected against known security vulnerabilities and exploits.
Data Backup and Recovery Planning
A resilient data backup and recovery plan is essential. In the event of a ransomware attack or other data-destroying malware, a good backup can be the difference between a minor inconvenience and a catastrophic loss. Regularly test your backups to ensure they are working correctly and that you can restore data quickly.
Employee Security Awareness Training
Employees are often the weakest link in a security chain. Regular security awareness training can teach employees how to spot phishing emails, use strong passwords, and follow secure browsing habits. Educating users on the risks and best practices significantly reduces the likelihood of a successful attack.
Adopting a Zero Trust Security Model
A zero trust security model operates on the principle of "never trust, always verify." It assumes that no user or device should be trusted by default, whether inside or outside the network perimeter. All access requests are authenticated and authorized before granting access, thereby limiting the lateral movement of malware within the network.
Malware Protection vs. Antivirus: What's the Difference?
While the terms are often used interchangeably, there are important distinctions between them. Antivirus software is a core component of malware protection, but it's not the complete solution.
| Feature | Antivirus Software | Malware Protection |
|---|---|---|
| Primary Goal | Detect and remove known viruses and a limited scope of malware. | Prevent, detect, and respond to a wide range of cyber threats, including viruses, ransomware, and fileless malware. |
| Detection Method | Primarily signature-based detection. | Multi-layered approach including signature-based, behavioral analysis, machine learning, and threat intelligence. |
| Scope of Protection | Endpoint-centric, focusing on files on a single device. | Endpoint-centric, focusing on files on a single device. |
| Capabilities | Basic scanning and quarantine. | Advanced capabilities like EDR, sandboxing, network traffic analysis, and incident response. |