- What is Multi-Extortion Ransomware?
-
Malware vs. Exploits
-
What is Ransomware as a Service (RaaS)?
- What is Malware vs. Ransomware?
- What Is Malware Protection? Best Practices for Modern Businesses
-
Expanding Targets for New SunOrcal Malware Variant
-
What Are Fileless Malware Attacks and “Living Off the Land”? Unit 42 Explains
What is Malware? Detecting, Preventing & Managing Threats
What Is Malware? Definition, Types, and Examples
Malware (short for malicious software) is any program or code intentionally designed to damage, disrupt, or steal from computer systems, networks, or data. Malware comes in many forms — including viruses, worms, trojans, ransomware, spyware, adware, and rootkits — all crafted by threat actors to compromise digital assets for financial, strategic, or disruptive purposes.
Unlike harmless bugs or glitches, malware is created with clear malicious intent. It can infect personal devices, enterprise servers, and even critical infrastructure. The rise of AI-powered malware and supply chain attacks makes it one of the most persistent cybersecurity challenges today.
Key Points
-
Common Vectors: Malware spreads through phishing emails, malicious websites, and unpatched software vulnerabilities. -
Layered Defense: Effective protection requires a multi-layered approach across endpoints, networks, and users. -
Business Impact: Malware attacks cause financial loss, regulatory fines, reputational damage, and operational downtime. -
Swift Response: A proactive incident response plan is critical for containment and recovery. -
Zero Trust: Adopting a Zero-Trust model limits lateral movement by verifying every user and device, ensuring a secure environment.
How Malware Works
Malware is typically created and distributed by:
- Cybercriminal gangs seeking profit through ransomware or data theft.
- Hacktivists aiming to disrupt organizations.
- Nation-state groups conducting cyberespionage.
It can:
- Steal sensitive information (passwords, financial records, intellectual property).
- Encrypt or destroy files to extort victims.
- Disrupt systems, networks, and services.

Types of Malware
Malware manifests in various forms, each with distinct operational characteristics and objectives. Malware is not a single entity but a category of software, each with its own specific function and attack method. They often collaborate in sophisticated, multi-stage attacks.
Extortion attacks have evolved in three waves, beginning with simple encryption, then adding data exfiltration and harassment, and now focusing on intentional disruption. In 2024, Unit 42 data showed that encryption was a tactic in 92% of extortion-related cases, data theft was present in 60%, and harassment in 13%.
| Type of Malware | How It Works | Example Impact |
|---|---|---|
| Virus | Attaches to legitimate programs/files and spreads when opened. | Corrupts files, system crashes. |
| Worm | Self-replicates across networks without user action. | Consumes bandwidth, slows systems. |
| Trojan | Disguised as trusted software, installs backdoors. | Remote control, data theft. |
| Ransomware | Encrypts files, demands payment for decryption. | Multi-million-dollar extortion attacks. |
| Spyware | Monitors user activity secretly. | Credential theft, financial fraud. |
| Adware | Delivers unwanted ads and may install additional malware. | Browser redirects, tracking. |
| Rootkit | Embeds deep in OS, hides attacker activity. | Long-term undetected access. |
| Fileless Malware | Lives in memory, uses system tools (e.g., PowerShell). | Evades antivirus, hard to detect. |
| Botnet | Network of infected devices under attacker control. | DDoS attacks, spam campaigns. |
How Malware Spreads: Common Attack Vectors
Malware doesn’t walk in the front door—it exploits weak spots. Phishing was the most common initial access vector for Unit 42's cases in 2024, accounting for about a quarter of incidents (23%).
- Phishing emails with malicious links/attachments.
- Compromised websites (drive-by downloads).
- Unpatched vulnerabilities in outdated software.
- Infected USB drives or removable media.
- Supply chain attacks in trusted vendors or updates.
Signs of a Malware Infection
Watch for these warning signs that a system may be infected with malware:
- Slow performance and frequent crashes
- Aggressive pop-ups or ads
- Locked or missing files
- Unusual network activity
- Locked files or ransom notes
- Browser redirects to unfamiliar sites
- Suspicious password resets
- Disabled antivirus or firewalls
How Malware Is Detected
Modern cybersecurity tools use multiple detection methods:
- Signature-Based Detection: This traditional method relies on a database of known malware signatures. Antivirus software scans files and processes for matches, effectively identifying previously cataloged threats.
- Heuristic Analysis: Heuristic engines analyze code for suspicious characteristics and behaviors that might indicate new or modified malware. This method can detect variants of known threats and some unknown ones as well.
- Behavioral Analysis: This technique monitors system processes, API calls, and network communications for anomalous activities. By establishing a baseline of normal behavior, security software can flag deviations indicative of malicious intent, even from fileless malware.
- AI-powered and Machine Learning: AI-driven security solutions leverage machine learning algorithms to analyze vast datasets of threat intelligence. These systems can identify complex patterns, predict potential threats, and provide real-time protection against novel and sophisticated malware, including zero-day exploits. According to Unit 42, in a simulated attack, using generative AI reduced the time to exfiltration from a median of two days to just 25 minutes.
- Sandboxing: Sandboxing involves executing suspicious files or code in a secure, isolated, and virtual environment. This allows security analysts to observe the malware's behavior without risking the integrity of the actual operating system or network.
- Endpoint Detection and Response (EDR): EDR solutions provide continuous monitoring of endpoint activities, collecting and analyzing data to detect and investigate suspicious events. They enable security teams to perform threat hunting, respond to incidents, and contain malware outbreaks more effectively.

Comprehensive Malware Protection Strategies
Comprehensive malware protection requires a multi-layered, proactive approach that combines technology, process, and people.
How to Prevent Malware
The following strategies reduce the attack surface and minimize opportunities for malicious software to infiltrate systems.
- Antivirus and Anti-Malware Software: Deploying reputable antivirus software and anti-malware solutions is fundamental. These tools offer real-time protection, regularly scan for threats, and quarantine or remove detected malicious software. Regular updates ensure they can identify the latest malware variants.
- Patch Management: Consistently applying security patches and updates to operating systems, applications, and firmware is critical. Threat actors frequently exploit known vulnerabilities in outdated legitimate software. A comprehensive patch management program closes these security gaps.
- Firewalls: Network and host-based firewalls control inbound and outbound network traffic, preventing unauthorized access and blocking malicious connections. They act as a barrier, filtering data packets based on predefined security rules.
- Email Security: Advanced email security solutions filter out malicious emails, detect phishing attempts, and block infected attachments before they reach end-users. These systems are crucial for mitigating a primary vector for malware delivery.
- Web Filtering: Implementing web filtering solutions prevents users from accessing known malicious websites or sites categorized as high-risk. This reduces the chance of drive-by downloads and exposure to browser-level exploits.
- Employee Training: Regular cybersecurity awareness training educates employees on recognizing phishing attempts, practicing strong password hygiene, and understanding the risks associated with suspicious links or downloads. Multifactor authentication should be enforced for all critical systems, as the absence of MFA was a contributing factor in 28% of cases involving the use of valid accounts for initial access (Unit 42 Global Incident Response Report 2025).
- Data Backup and Recovery: Maintaining regular, isolated, and verified backups of critical data is crucial for protecting against ransomware and ensuring overall business continuity. In the event of a successful malware attack, clean backups enable rapid recovery and minimize data loss.
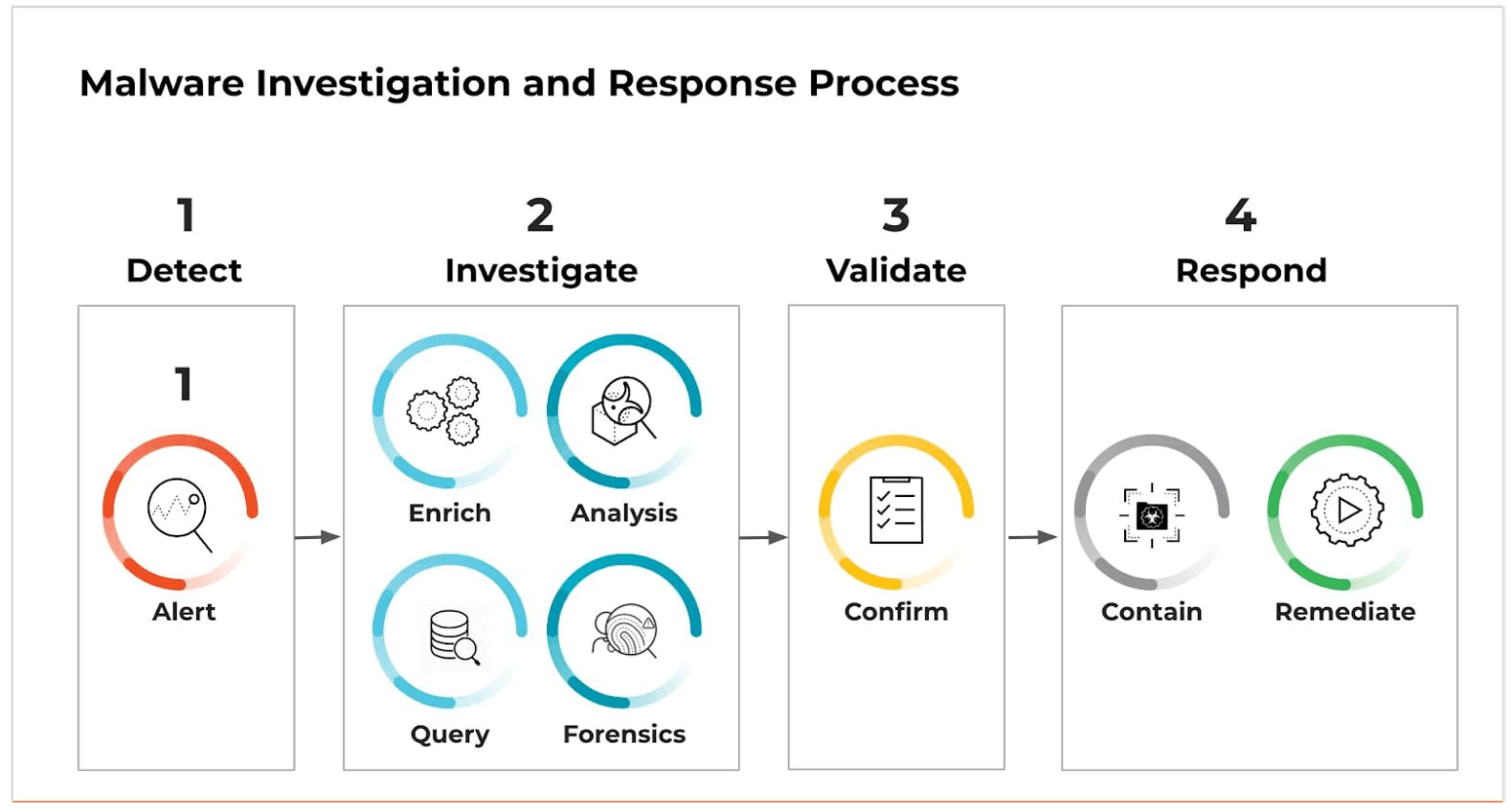
Incident Response and Malware Removal
Despite proactive measures, malware infections can occur. A well-defined incident response plan is vital for containing, eradicating, and recovering from an attack.
As attacks get faster, a quick response is more critical than ever. In 2024, the median time to exfiltration was about two days, and in nearly one in five cases (19%), data exfiltration occurred in less than one hour.
- Isolation: Immediately disconnect the infected device or segment the compromised network to prevent the malware from spreading further. This containment step is crucial in limiting the scope of the incident.
- Identification: Thoroughly investigate to determine the type of malware, its entry point, and the extent of the compromise. This involves forensic analysis and leveraging threat intelligence.
- Removal: Use specialized malware removal tools and processes to eradicate the malicious software from all affected systems. This may involve cleaning the operating system, reinstalling software, or restoring from clean backups.
- Recovery: Restore systems and data from trusted backups, reconfigure security settings, and verify that all traces of the malware have been removed. This phase focuses on returning to normal operations.
- Post-Incident Analysis: Conduct a comprehensive review of the incident to identify root causes, assess the effectiveness of existing defenses, and implement improvements to prevent future occurrences. This continuous learning cycle strengthens the overall security posture.
Business Impact of Malware
For security leaders and C-suite executives, malware protection extends beyond technical implementation; it is a strategic imperative for ensuring business continuity, maintaining data integrity, and upholding stakeholder trust. The impact of a successful malware attack can be far-reaching, affecting an organization's financial health, reputation, and operational capabilities.
Financial Costs and Regulatory Fines
- Ransom Payments: Paying a ransom can be a significant financial burden, with some attacks demanding millions of dollars. The median initial extortion demand increased by nearly 80% to $1.25 million in 2024.
- Incident Response Costs: The process of containing, investigating, and remediating a malware attack is expensive. It often requires hiring external forensics teams and legal counsel.
- Regulatory Fines: In the wake of a data breach or data-stealing malware attack, organizations may face substantial fines under regulations such as GDPR or HIPAA.
Operational Disruption and Downtime
Malware can bring business operations to a complete halt. A ransomware attack can lock up servers and endpoints, making it impossible for employees to work. This downtime can last for days or weeks, resulting in missed deadlines, reduced productivity, and substantial revenue loss.
Reputational Damage and Loss of Customer Trust
An apparent malware attack can erode customer trust and damage a brand's reputation. When customers learn that their data has been compromised, they may take their business elsewhere. The long-term reputational damage can be more costly than any ransom payment or regulatory fine.
Emerging Trends: Malware in the AI Era
- AI-driven malware adapts faster and evades detection.
- Cloud & SaaS malware targets collaboration platforms.
- SMBs at risk: Smaller organizations are facing a rise in attacks due to weaker defenses.
- Multi-pronged attacks are becoming increasingly common, with 70% of incidents in 2024 affecting three or more fronts, including endpoints, networks, and the cloud.
Malware FAQs
Malware is a broad term for any malicious software. Viruses, worms, and trojans are specific types of malware, and they differ mainly in how they spread and operate:
- Malware: The general category for all malicious software.
- Virus: Attaches to a legitimate file and requires a user to open it to spread.
- Worm: Self-replicates and spreads across networks on its own, without a user's help.
- Trojan: Disguises itself as a harmless program to trick users into installing it, often creating a backdoor for an attacker to use.

